Cloud-Based Computer Vision System for Grocery Shelf Management
Project Overview
We partnered with a major food retail chain to develop a privacy-conscious computer vision system for automated shelf monitoring. The solution needed to process in-store imagery at scale while addressing critical considerations: GDPR compliance for any incidental capture of customer images, secure data handling for proprietary planogram data, and operational efficiency through edge processing. The system automates planogram compliance checks, out-of-stock detection, and generates actionable tasks for store teams — all while maintaining strict data governance.
Privacy & Data Governance
Retail computer vision inherently involves processing images that may incidentally capture individuals. Our architecture was designed with privacy as a foundational requirement:
- Privacy-by-Design Architecture: Edge processing means raw images never leave the store premises. Only structured metadata (shelf positions, product counts, compliance scores) is transmitted to central systems.
- Automatic Face/Person Blurring: Real-time detection and blurring of any individuals captured in frame before any image storage or analysis.
- Data Retention Controls: Raw images deleted within 24 hours after processing. Aggregated analytics retained per configurable policy. Full audit trail of data lifecycle.
- GDPR Documentation: Data Protection Impact Assessment (DPIA) completed. Processing purposes documented. Lawful basis established under legitimate interest with balancing test.
- Signage & Transparency: Template in-store signage provided explaining the system's purpose and data handling, supporting the client's transparency obligations.
Technologies Used
The stack was selected for accuracy, security, and cost-effective scalability:
- YOLOv8 + Custom Detection Head: Fine-tuned object detection achieving 96.2% mAP on client's product catalogue. Optimised for real-time inference on edge hardware.
- NVIDIA Jetson Edge Devices: On-premises inference with secure boot, encrypted model weights, and tamper detection. OTA update capability with signed firmware packages.
- AWS (EC2 + S3 + SageMaker): Cloud infrastructure for model training, A/B testing, and centralised analytics. VPC isolation with private endpoints. S3 encryption with customer-managed keys.
- TensorRT Optimisation: Model compilation for edge deployment achieving 45 FPS inference on Jetson AGX Orin while maintaining accuracy.
- MLflow: Model versioning, experiment tracking, and deployment pipeline with full audit trail of model lineage.
Challenges and Solutions
The project required solving technical, operational, and compliance challenges:
-
Privacy Compliance
- Challenge: Processing in-store imagery while ensuring GDPR compliance for any incidental capture of customers or staff.
- Solution: Edge-first architecture with on-device person detection and blurring. Raw images never leave store premises. Completed DPIA with client's data protection team.
-
Edge Security
- Challenge: Protecting model intellectual property and preventing tampering on physically accessible edge devices.
- Solution: Secure boot chain, encrypted model weights (AES-256), TPM-based key storage, and tamper detection logging. OTA updates with signed packages and rollback capability.
-
Multi-Environment Consistency
- Challenge: Maintaining accuracy across 200+ stores with varying lighting, camera angles, and shelf configurations.
- Solution: Human-in-the-loop training tool enabling store-specific fine-tuning. Automated drift detection alerts when accuracy degrades below threshold.
-
Operational Cost Control
- Challenge: Processing thousands of images daily without prohibitive cloud computing costs.
- Solution: 95% of inference runs on-edge with only aggregated metrics transmitted to cloud. Cloud costs reduced by 80% versus cloud-only architecture.
Security Architecture
- Edge Device Security: Secure boot, encrypted storage, tamper-evident logging. Devices authenticate to central services via certificate-based mutual TLS.
- Network Security: All traffic encrypted (TLS 1.3). Edge devices communicate only with designated endpoints. No inbound connections to edge devices — all communication initiated outbound.
- Access Control: RBAC for management console. Store managers see only their locations. Regional managers see aggregated data. Audit logging of all administrative actions.
- Model Protection: Encrypted model weights with hardware-bound decryption keys. Model extraction attacks mitigated through obfuscation and integrity verification.
System Features
Our team successfully delivered a high-accuracy, automated system that:
-
Mobile Application:
Store managers and back-office teams could access real-time data, task notifications, and visual analytics on shelf performance.
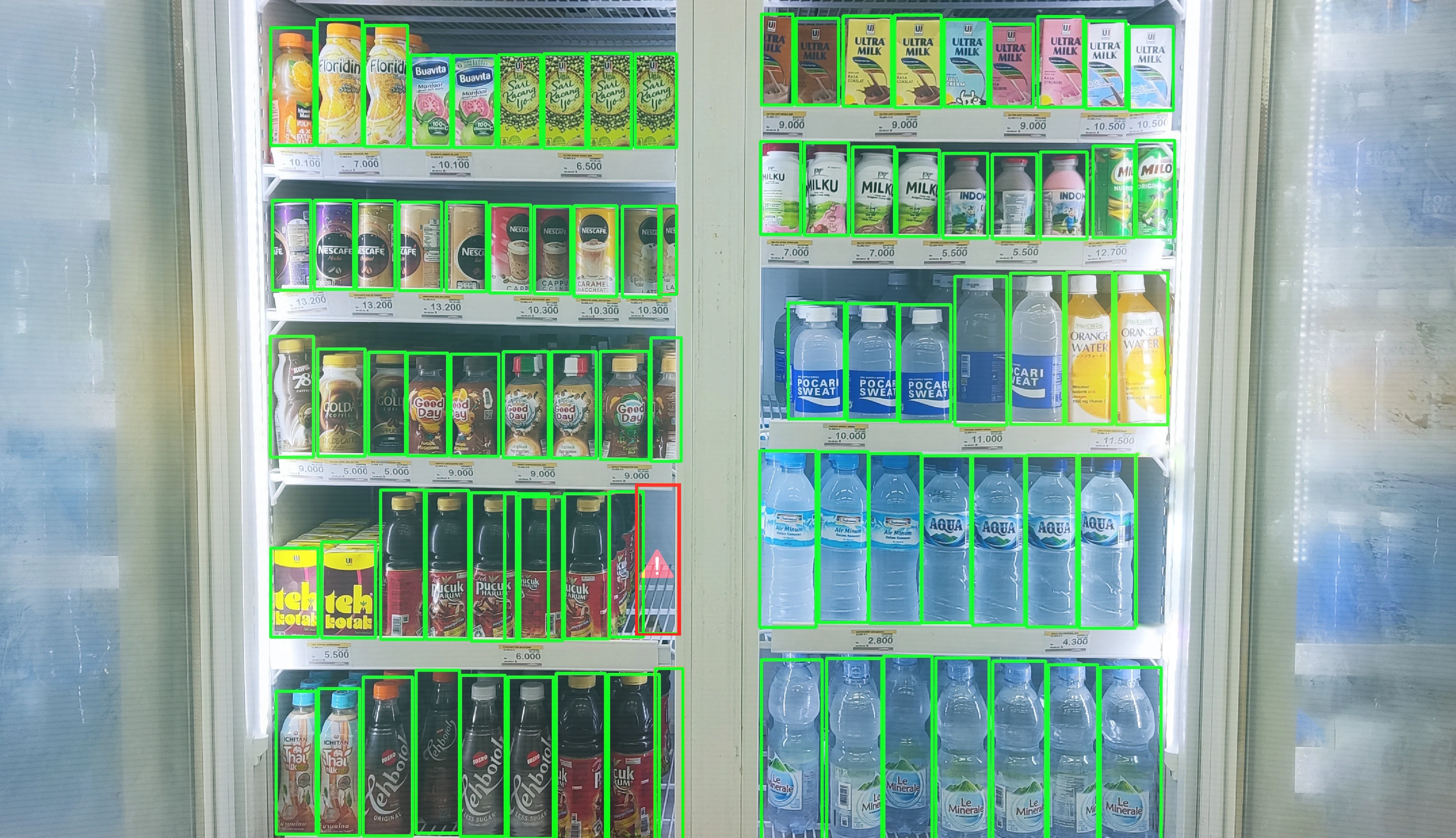
-
Training Tool:
A user-friendly interface allowing the client to train models for new product categories or adapt to seasonal planograms.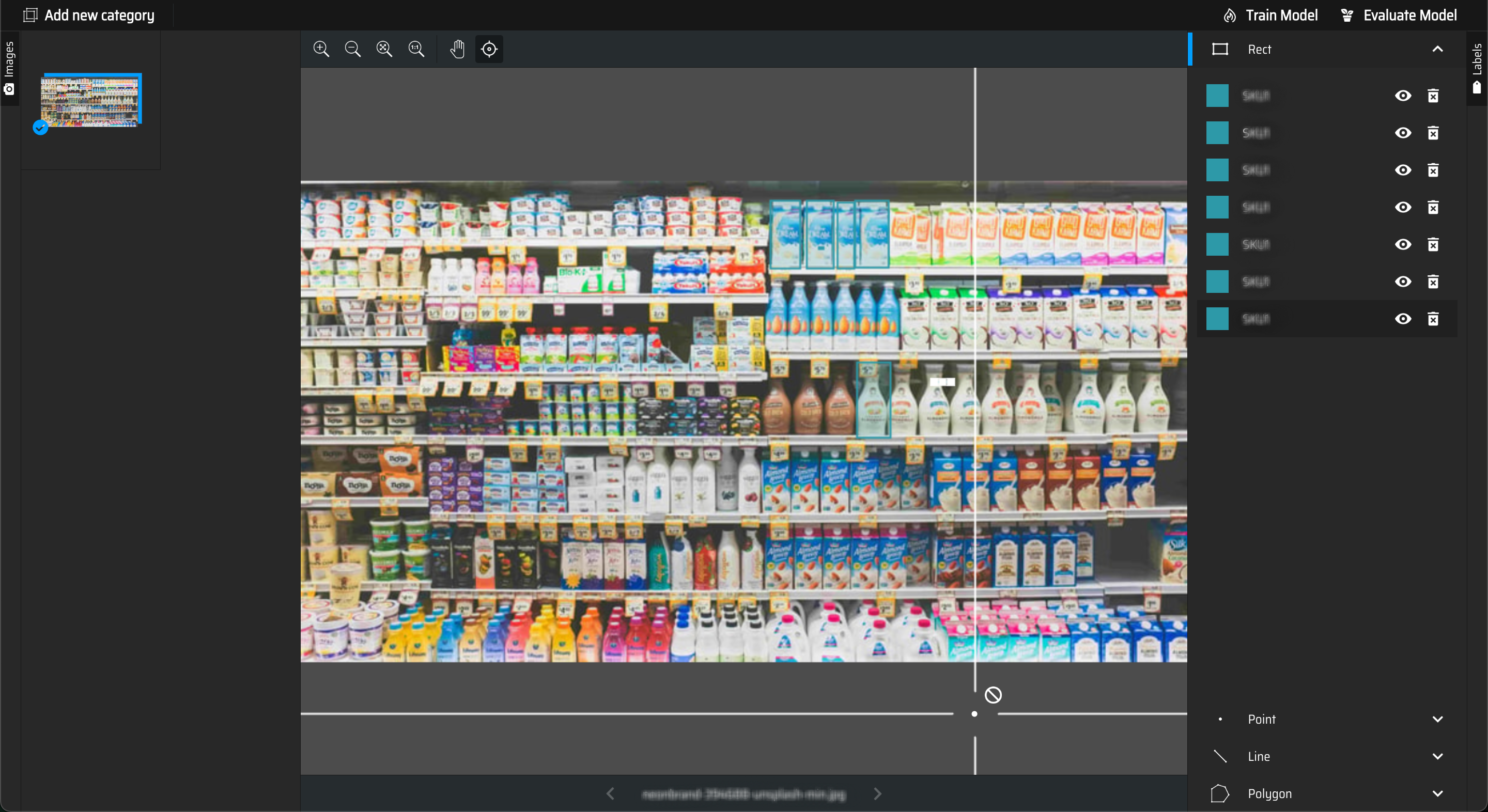
-
Dashboards:
Centralized analytics for monitoring planogram compliance, out-of-shelf occurrences, and performance trends.
Results
- 20% Reduction in Empty Shelf Time: Automated detection and immediate task generation enables faster restocking, directly improving product availability.
- 1-3% Revenue Uplift: Improved shelf availability in key product categories translated to measurable sales increases.
- 80% Cloud Cost Reduction: Edge-first architecture dramatically reduced ongoing infrastructure costs versus cloud-only alternatives.
- Zero Privacy Incidents: 18 months in production across 200+ stores with no data protection complaints or incidents.
- 96.2% Detection Accuracy: Maintained high accuracy across diverse store environments through continuous training and drift monitoring.
Why NodeNova
Retail computer vision requires balancing operational value with privacy obligations and security requirements. Our approach is distinguished by:
- Privacy-First Architecture: We design for data minimisation from the start. Edge processing, automatic anonymisation, and strict retention policies are foundational — not afterthoughts.
- End-to-End Security: From secure boot on edge devices to encrypted cloud storage, we address the full attack surface of distributed AI systems.
- Regulatory Awareness: We understand GDPR, ICO guidance on AI, and retail-specific considerations. Our documentation supports your compliance obligations.
- Production Engineering: Not research projects — production systems with monitoring, alerting, and documented operational procedures.
Long-Term Impact
The partnership continues with ongoing system evolution:
- Geographic Expansion: Architecture designed for multi-region deployment with data residency controls per jurisdiction.
- Model Evolution: Quarterly model updates incorporating new product lines and seasonal variations, deployed via secure OTA.
- Feature Expansion: Roadmap includes promotional display compliance, competitor product detection, and integration with inventory management systems.
- Continuous Compliance: Regular privacy reviews and security assessments ensure the system remains aligned with evolving regulatory expectations.